Security
Arista Cloud Network Data Security tools provide next-generation network firewalls featuring visibility and cybersecurity monitoring powered by Arista Networks CloudVision
Overview:
From network security to secure networks
A new age of edge-less, multi-cloud, multi-device collaboration for hybrid work has given rise to a new network that transcends perimeters. As hybrid work models continue to gain precedence through the new network, it has become vital for organizations to address the cascading attack surface. Continuously evolving cyber threats can no longer be mitigated by reactionary bolt-on security measures or perimeter firewalls. Instead, organizations need security to permeate the underlying network infrastructure.
Security measures need to pivot from reactive to a more proactive approach of continuous contextual network monitoring that ensures threats are detected and mitigated before an expansive data breach.
Being secure in the new network, the zero trust way.
A zero trust networking approach to security is paramount for organizations looking to build a robust cybersecurity ecosystem today. Based on the premise of explicit trust, zero trust security ensures complete visibility and control over any enterprise network activity, regardless of which device, application, or user is accessing that resource.
This paradigm shift has prompted best-in-class enterprises to bake security into the core of their network infrastructure. Implementing security at this layer reduces operational costs and complexity and represents the most effective way to track and successfully manage threats coming in from the wider attack surface.
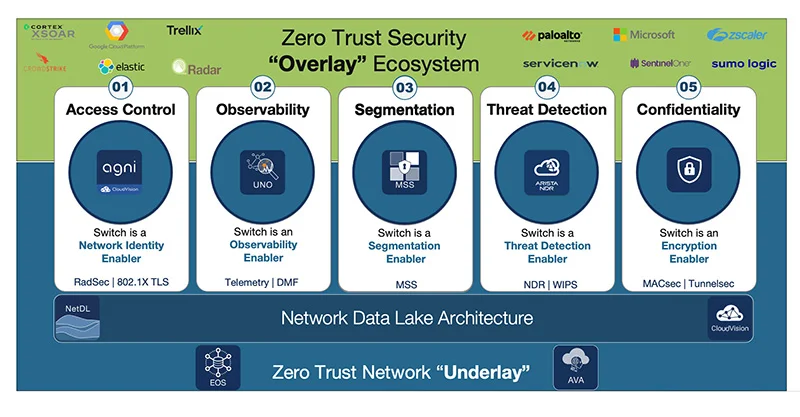
Zero Trust Networking
Arista’s suite of security solutions helps customers accelerate their journey towards zero trust maturity. Based on the CISA Zero Trust Maturity Model, Arista supports all the essential functions CISA recommends for the network: network segmentation, network traffic management, traffic encryption, and network resilience along with controls for visibility and analytics, automation and orchestration, as well as governance.
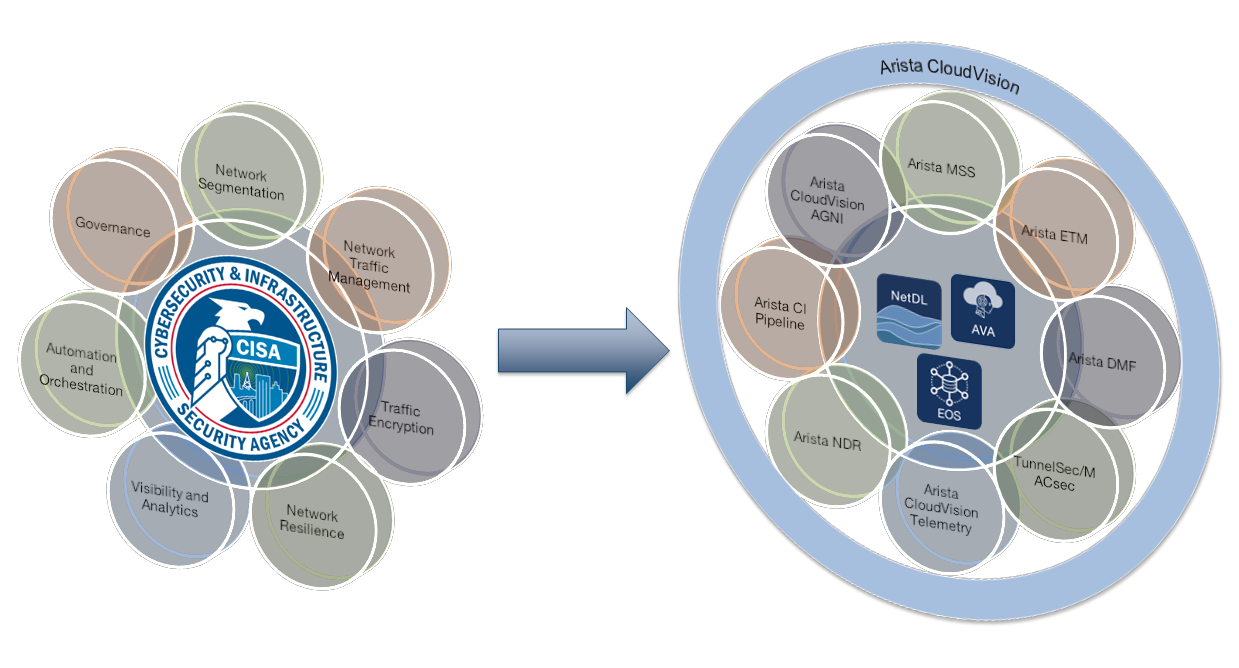
In fact, the network can be the center of any organization’s CISA zero trust maturity efforts.
The network is pervasive – every communication hits the network at some point enabling observability, threat detection, and access control to be transparently enabled. This provides risk mitigation for the legacy devices, workloads, and data stores that cannot be easily “ZT-fied.” As a result, implementing zero trust on the network can accelerate the overall zero trust program and buy time to address deeper challenges in the other domains – like data or workloads.
The network does not care whether the devices are managed or unmanaged -- instead, it can identify those devices and apply policies for authentication and authorization, irrespective of what they are and where they are currently.
The network is much more homogenous than devices, workloads, users, data, etc. Protocols like TCP/IP are universal unlike the complexity involved with different operating systems or application server software.
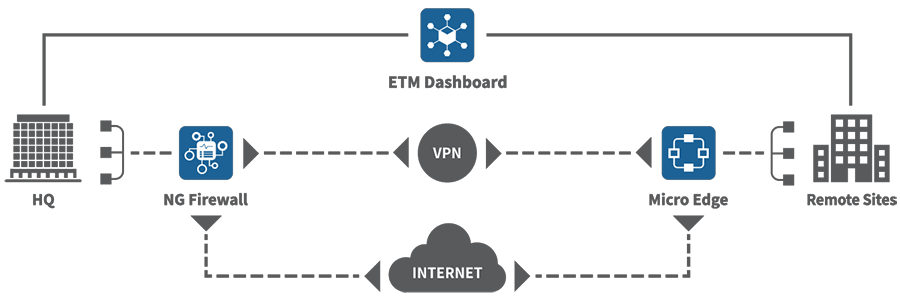
Of course, some would argue the network does have blind spots, for instance, remote endpoints or branches that do not backhaul network traffic but route directly to the Internet. These setups may not hit the organization’s traditional network and thus be “invisible” to the organization’s zero trust controls. Any zero trust networking architecture must therefore act as a strong network underlay and support tight workflow integrations with complementary security overlay solutions such as endpoint detection and response or zero trust network access technologies.
Arista Enables Universal Zero Trust Networking
As evidenced by the Universal Cloud Network (UCN) architecture, Arista helps customers build networks that are secure by design. Arista’s zero trust portfolio eliminates the need for several network monitoring and security tools by delivering a unified and integrated architecture that provides real-time visibility of the threat posture across the network and the ability to take action. Arista is uniquely positioned to deliver these capabilities across various networks: from the campus to the data center and the cloud.
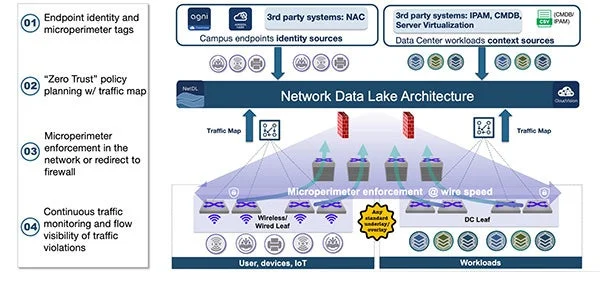
Arista's Multi-Domain Segmentation Service (MSS) is a comprehensive microsegmentation solution that provides fine-grained security policies based on microperimeters defined around the identity of endpoints or applications.
MSS offers a consistent architecture across multiple network domains, is both network and endpoint-agnostic, and enables the distributed enforcement of stateless policies at wire speed within the Arista EOS-powered switches or can redirect traffic to a third-party firewall for stateful L4-7 inspection. Arista MSS thus enables lateral segmentation offloading the capability from firewalls that would have to be explicitly deployed for this purpose.
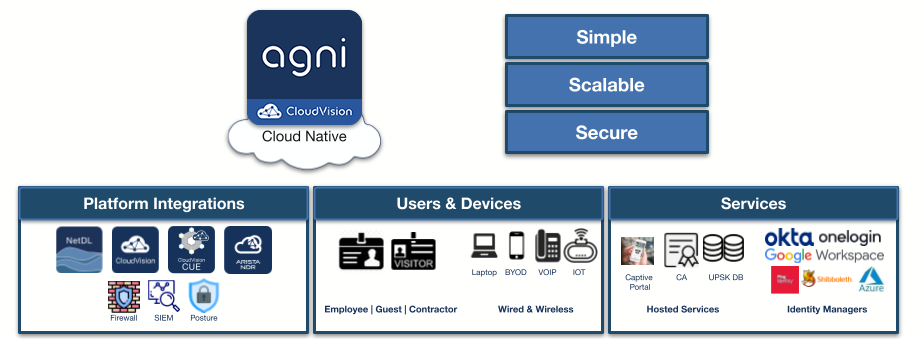
Arista MSS also automates the management of microperimeters by connecting to external sources and dynamically identifying and tagging the endpoints and workloads. To get this information, Arista MSS can connect to various external sources, such as NAC, CMDB, IPAM and server virtualization systems.
Network Traffic Management
The network traffic management function requires the ability first to identify applications and then classify them for optimal user experience. These capabilities are operationalized through quality of service and bandwidth reservations as well as granular monitoring policies. Arista EOS provides robust quality of service features as well as the ability to classify the traffic for appropriate prioritization within the network relative to other applications. The Arista DANZ Monitoring Fabric (DMF) enables IT operators to pervasively monitor all user, device/IOT, and application traffic (north-south and east-west) by gaining complete visibility into physical, virtual, and container environments. Deep hop-by-hop visibility, predictive analytics, and scale-out packet capture — integrated through a single dashboard — provides unprecedented observability to monitor, discover, and troubleshoot network and application performance issues, as well as accelerates discovery of root causes of security breaches and other outages.
Traffic Encryption
Arista network infrastructure natively supports encryption capabilities such as MACsec and TunnelSec. These capabilities, implemented on the switches, enable organizations to encrypt data to and from legacy applications and workloads without changing those systems but instead relying on the network to protect data from unauthorized access, interception, and tampering.
TunnelSec uses industry-standard protocols like IPSec and SSL/TLS to establish secure tunnels across any network, including the public internet and thus enable secure communication and data exchange between remote locations. This is particularly useful for organizations with multiple branch offices or data centers that need to communicate securely with each other over a public network.
MACsec operates at the link layer of the network stack and provides data encryption between campus or data center network devices. MACsec is used to secure communications between devices on the same physical network, such as within a data center.
Network Resilience
Arista EOS and CloudVision bring a modern approach to continuous application delivery and performance. The key to resilience in a zero trust context lies in the ability to dynamically expand or reduce with network demands. For instance, this could mean having the ability to burst and use a utility cloud when the demand is higher or availability is threatened. Similarly, network operations could use capacity from disaster recovery sites or backup data centers. Arista’s Cloud Vision and EOS work hand in hand to dynamically provide onboarding and connectivity to any public utility clouds securely and with optimal performance. In many instances, customers striving for zero trust maturity in this function deploy data centers in active/active configuration using robust EOS features such as EVPN that provide the entire capacity as a single virtual data center while still providing geo-specific fault tolerance. CloudVision, in turn, provides a single pane of glass management for both the traditional data center as well as the hybrid cloud.
Visibility and Analytics
Arista NDR is an AI-enabled platform that analyzes billions of network communications to autonomously discover, profile, and classify every device, user, and application across the new network—perimeter, core, IoT, and cloud networks. Based on this deep understanding of the attack surface, the platform detects threats to and from these entities while providing the context necessary to respond rapidly.
Arista NDR can deliver visibility and analytics enterprise-wide by utilizing existing deployed switches as network security sensors. As a result, organizations can benefit from broad situational awareness without the need to deploy additional network tapping infrastructure or network visibility solutions, but instead by relying on infrastructure that is already deployed. This is especially important in campus and branch locations where such components can be complex to deploy and maintain without dedicated rack space and local IT expertise.
Automation and Orchestration Capability
The Arista CI Pipeline provides an advanced CI environment for managing network and security operations, built upon the visibility delivered by the Arista CloudVision platform. This capability, along with Arista Validated Designs (AVD), greatly simplifies and enhances the automation of network and security operations workflows.
Governance Capability
CloudVision Arista Guardian for Network Identity™(CV AGNI) is a software-as-a-service network access control (NAC) solution that simplifies the onboarding and ongoing governance of network identity across users, their associated devices, and the internet-of-things for both wired and wireless networks. CV AGNI uses existing identity providers such as Microsoft Azure AD or Okta. It acts as the policy decision point (PDP) and policy enforcement point (PEP), both critical for an effective zero trust architecture. CV AGNI performs dynamic authorization via real-time posture assessments based on data from Arista NDR and third-party technologies such as endpoint detection and response solutions. Based on these assessments and policies defined by the organization, unauthorized entities or those violating security policies can be automatically quarantined.
Securing the New Network with a Unified Security Strategy
Networks have evolved in the last 20 to 30 years, but network security still hasn’t. Siloed traditional models persist and organizations are left with gaping holes in their visibility across the campus, branch, and data center networks. Most organizations have several diverse cybersecurity solutions that are patched together to combat known threats. Arista’s solutions are designed to scale and support a variety of networks. Arista’s security approach allows organizations to set up enforcement and access control mechanisms via scalable admission control, encryption, and segmentation approaches; enable analytics that uncover malicious intent as early in the attack lifecycle as possible, and deliver autonomous response and guidance for remedial action via microsegmentation capability. Arista’s security solutions support out-of-the-box automated integrations with the rest of the infrastructure while also delivering the necessary decision-support data to the human analyst.